More than 9100 open source projects and 51000 developers use Coverity Scan
“I started with very low expectations as most commercial tools only find things cppcheck will find, too. But coverity-scan actually found what brought down the performance of my program the most and a few handful of bugs.”
“From my experience, I think that Coverity improves the software quality of the NNStreamer project.”
“Perfect for our small team of developers . With Coverity we have a good program which supports us .”
“Coverity remains the single most useful tool I've used.”
“Coverity's static source code analysis has proven to be an effective step towards furthering the quality and security of Linux”
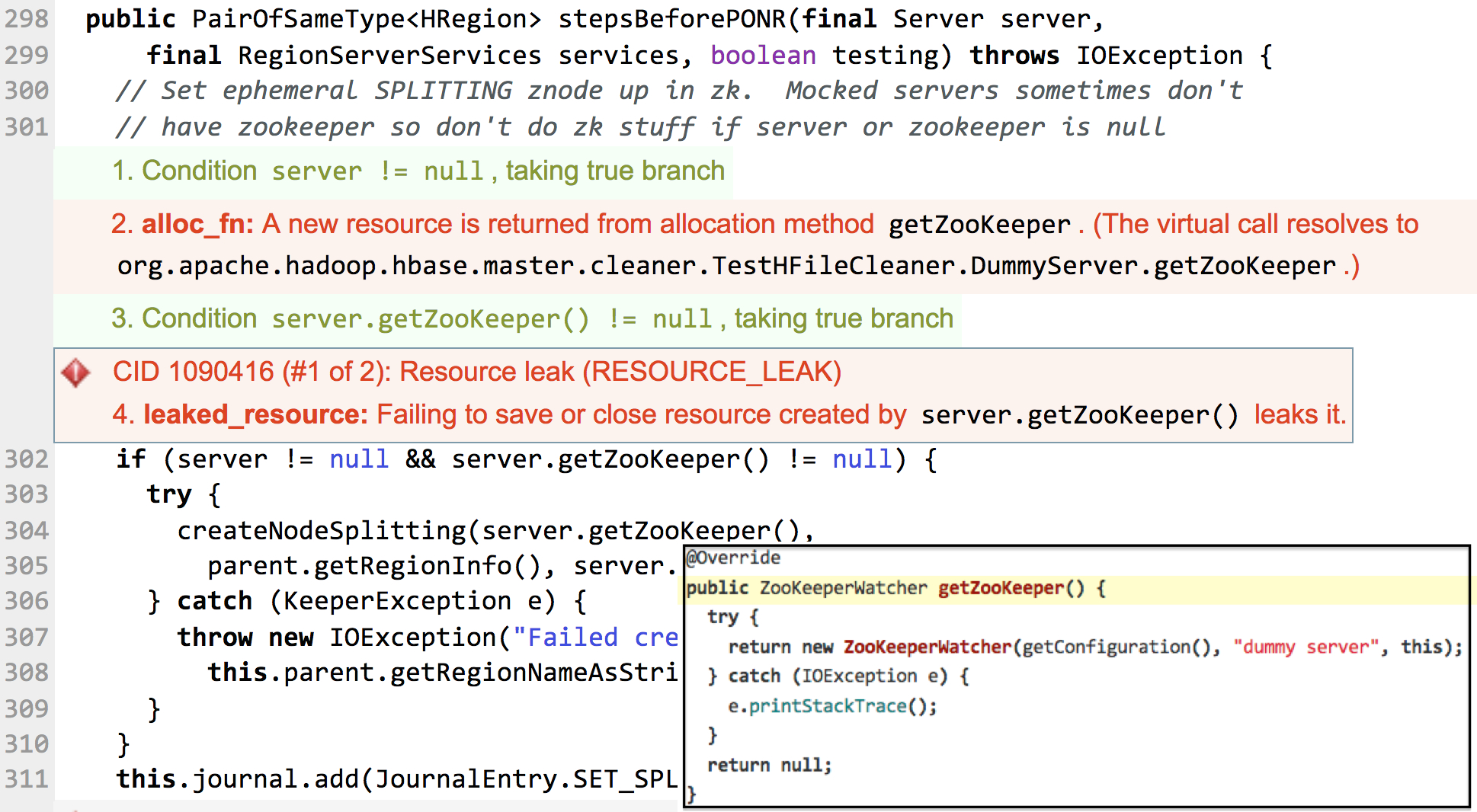
“Ah, that's cool. Pretty neat that an automated tool can catch mutex lock problems in conditional statements wrapped in macros! I'm impressed.”
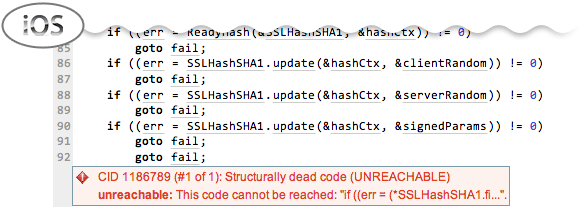
“You have a very good product and provide a great service to the open source community (certainly to the Linux kernel community).”
“Thank you guys for making such an awesome tool accessible to the open source community!”
Announcements
Coverity Upgrade to 2024.6
2025 Jan 7
Attention SCAN users! We will be upgrading the Coverity tools in SCAN on Saturday, 11th Jan to make this free service even better. The SCAN team has been hard at work stabilizing the service and getting ready for this upgrade.
SCAN will be unavailable during the upgrade, locking registration and triage, and halting builds. Defect data will be unavailable at that time. The upgrade is expected to take up to three hours.
After the upgrade, a new version of the Coverity build package will be available for download. Be sure to download the new build package.
Full details of new features are available at the Community Site.
Updates
Supported Versions
Versions 2023.09 and older will no longer be supported after the upgrade.
The currently supported versions are:
- 2024.6.1
- 2023.12.2
Users are encouraged to download the latest tools in Downloads.
Going forward, only the latest two releases will be supported. This means projects should be expected to update their tools approximately once a year (or more frequently if you want the latest features/support).
Scan Spotlight Projects
2023 July 23
The following nominated projects have recent defect resolutions:
| libreoffice | qemu | hwloc | performancecopilot-pcp |
| stress-ng | zephyr | tdengine | synchronet |
| wireshark | wine | bro | ffmpeg |
| mesa | scummvm | kicad | apache-traffic-server |
New API endpoint to upload larger builds
2023 June 15
The current api request used to automate uploading a Project build has a limit of 500MB.
We have added a new API endpoint to facilitate uploading larger builds.
Please check the Submit Build page for more details.
Build Limits
The number of weekly builds per project are as follows:
- Up to 28 builds per week, with a maximum of 4 builds per day, for projects with fewer than 100K lines of code
- Up to 21 builds per week, with a maximum of 3 builds per day, for projects with 100K to 500K lines of code
- Up to 14 builds per week, with a maximum of 2 build per day, for projects with 500K to 1 million lines of code
- Up to 7 builds per week, with a maximum of 1 build per day, for projects with more than 1 million lines of code
Interested in open source quality?
Check out what's happening with your favorite open source projects.
Find Your Project